Cybersecurity researchers at ThreatFabric have discovered a new mobile malware family called "Brokewell" that poses a significant threat to Android users.
The malware spreads through fake browser update pages designed to trick victims into downloading and installing malicious Android applications. Once installed, Brokewell can perform overlay attacks to capture user credentials, steal session cookies, and log all user actions including touches, swipes, text input, and applications opened.
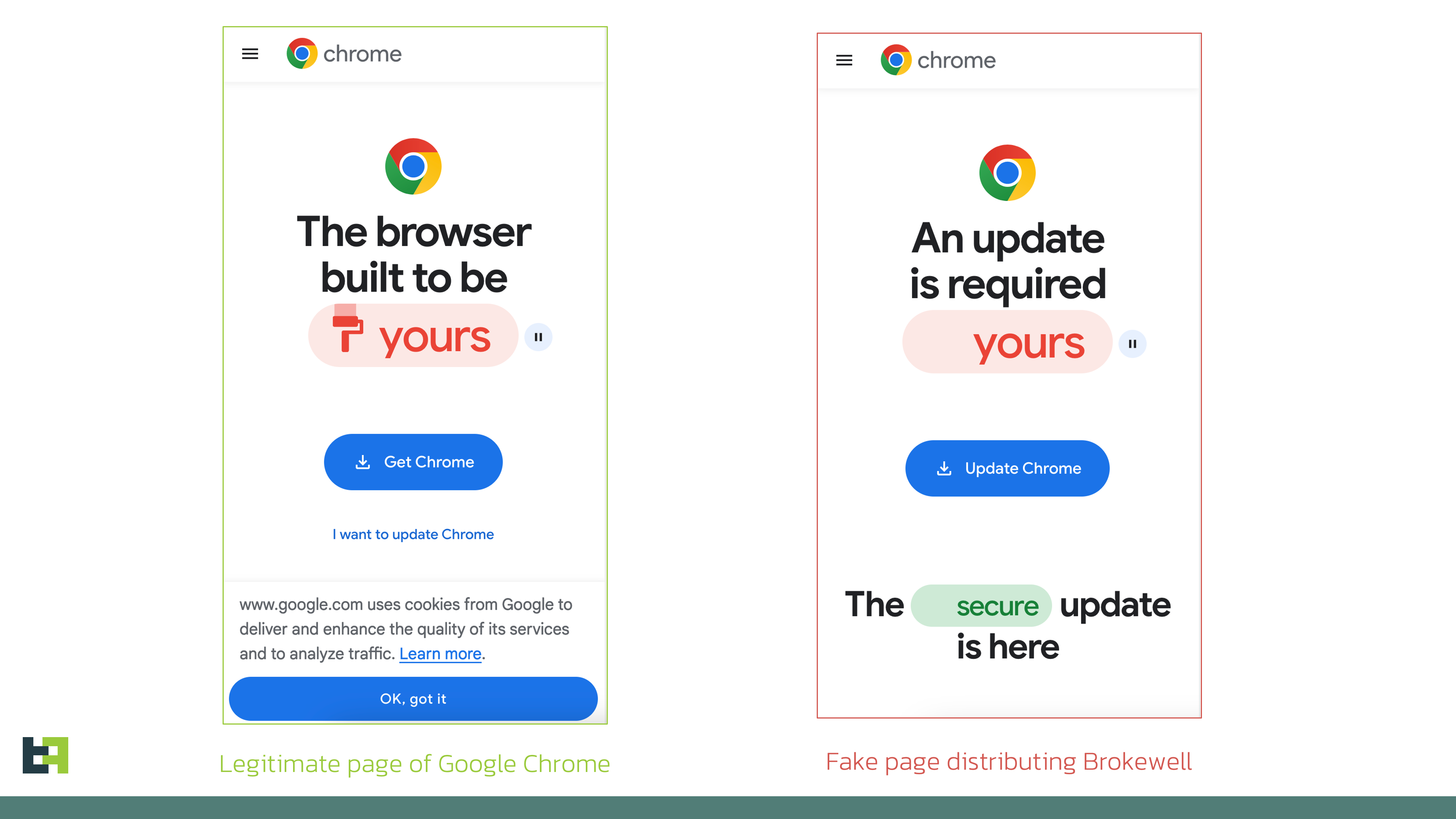
Brokewell provides attackers with a wide range of remote control capabilities over infected devices. It can perform actions like clicking elements, scrolling, swiping, typing text, taking screenshots, and streaming the device's screen. This level of control enables the attackers to carry out fraudulent activities directly on the victim's device.
The malware appears to be under active development, with new commands being added almost daily. Researchers have observed prior campaigns by Brokewell targeting financial services and authentication applications.
Brokewell's creator, identified as "Baron Samedit," has also developed an Android loader tool designed to bypass restrictions on accessibility services in Android 13 and later versions. This tool has been made publicly available, potentially lowering the entry barrier for other cybercriminals to distribute mobile malware on modern devices.
Malware families like Brokewell pose a significant risk to customers of financial institutions, as they can facilitate successful fraud cases that are difficult to detect without proper fraud detection measures in place.
Are you interested in buying a Smartphone?
We deliver nationwide













